
Article written by Axis Geffen
We cannot talk about countersurveillance without considering the role of digital electronic devices. Tiny cameras, listening devices, tracking devices and other electronics can seamlessly monitor a subject and record the information locally (on a storage device) or remotely (by transmitting to a receiver or the cloud). In the event of such a device or devices being employed, a much more sophisticated approach is required to combat this surveillance technology, and we call that Technical Surveillance Counter Measures (TSCM).
TSCM is conducted by specialists using very expensive technical equipment, and it always involves a thorough physical search as well. This type of inspection can take anywhere from a few hours, to days or weeks to complete depending on the area to be checked (swept), how many specialists are present, how much clutter exists, the level of interference encountered and/or additional devices/equipment that may be involved.

These inspections are conducted in real time and are conducted within specific frequency ranges. The majority of these inspections are conducted between 100KHz and 8GHz; however, depending on the anticipated threat, can enter into impossibly high frequencies or ultra-low frequencies such as phone lines, cable lines or voltage lines. Many people are surprised to learn that their conversations can literally be sent out of their secure facility via common power lines used for everyday electricity. This technique is used by many “installers.”
One of the most interesting things about “installers” of these devices is that they range from fairly unskilled to former espionage experts. As such, looking for these devices is not a simple job or reasonably accomplished by an untrained specialist. For this reason, it is always best to defer to your lawyer for assistance in locating help if you believe you’ve been “bugged.”
How Does TSCM Work?
It is not impossible for a specialist to work alone but it is far more common to see TSCM conducted by teams of two or more people at a time. The TSCM search normally works like this:
- A member of the team attends the site in advance or requests detailed photographs of the areas in order to determine the resources required
- Once the sweep is underway, the team will arrive (generally in non-descript vehicles) and carry a number of cases into an area near, but not generally within, the inspection site and begin setting up
- The team is usually briefed in advance and each member is aware of their specific role or function. All members tend to carry notepads and pens to record findings
- From this point forward a physical inspection is conducted in which every outlet, fixture, socket, wall and floor is examined
- When possible, another specialist will simultaneously monitor electronic signals being transmitted to/from/through the area and they will each be flagged, identified, verified and either hunted or permitted to continue as “friendly”
- The team will periodically be in contact with each other as required to identify anomalies. When potential devices are found, the location will be documented and the senior-most investigator will be called upon to further inspect and decide what happens with each item
What happens if the team finds something?
Many would assume that once a bug is found, the job is over. But that is actually just the beginning. Each device is identified, and the circumstance is noted. From there, a discussion is held with the lawyer and/or client to determine if the bug will remain and be used to disseminate false information; if the bug will remain and police will be called in, or if the bug will be removed.
Not every bug removed is reported to the police; in some cases, a client does not wish to pursue legal action – it is the client’s right to decide on the appropriate course of action.
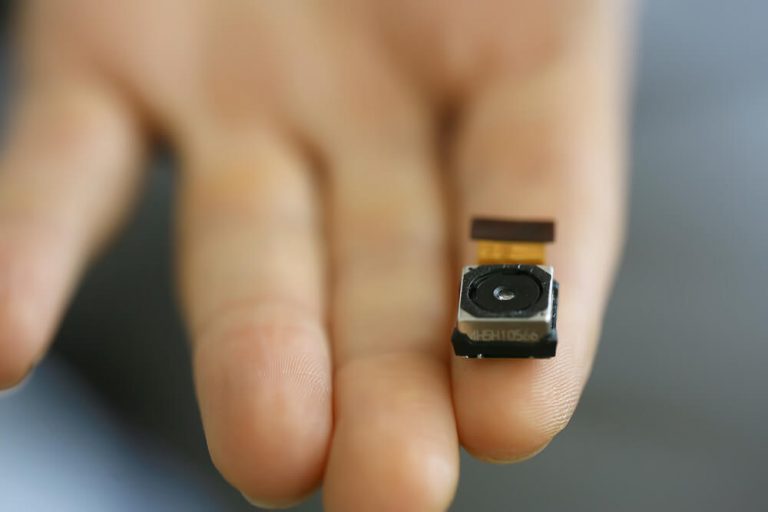
After a bug is found, the process is continued to ensure there are no additional devices. There is often more than one device installed. This process is repeated in the client’s home, office, vehicle(s) and any other location that may be conducive to monitoring. Audio and video recordings can be conducted very well within a vehicle in addition to third party GPS tracking of the vehicle. Often, this involves hard drives for long term recording.
Is countersurveillance worth it?
Countersurveillance activities are only as good as the people conducting them, and are only representative of the time at which they are conducted. A search in the day may yield different results at night, a running car may show different results than one that is turned off. For this reason, it is critical to allow your team to work flexibly and without interruption.
If something is found, you will be notified; if nothing is found, you will be notified. Trust in your team. Your interests are the only ones they have in mind.
%201.png?)
